We are thrilled to announce the release of [Ory Kratos v1.3.0](https://www.ory.sh/kratos)! This release includes significant updates, enhancements, and fixes to improve your experience with Ory Kratos. 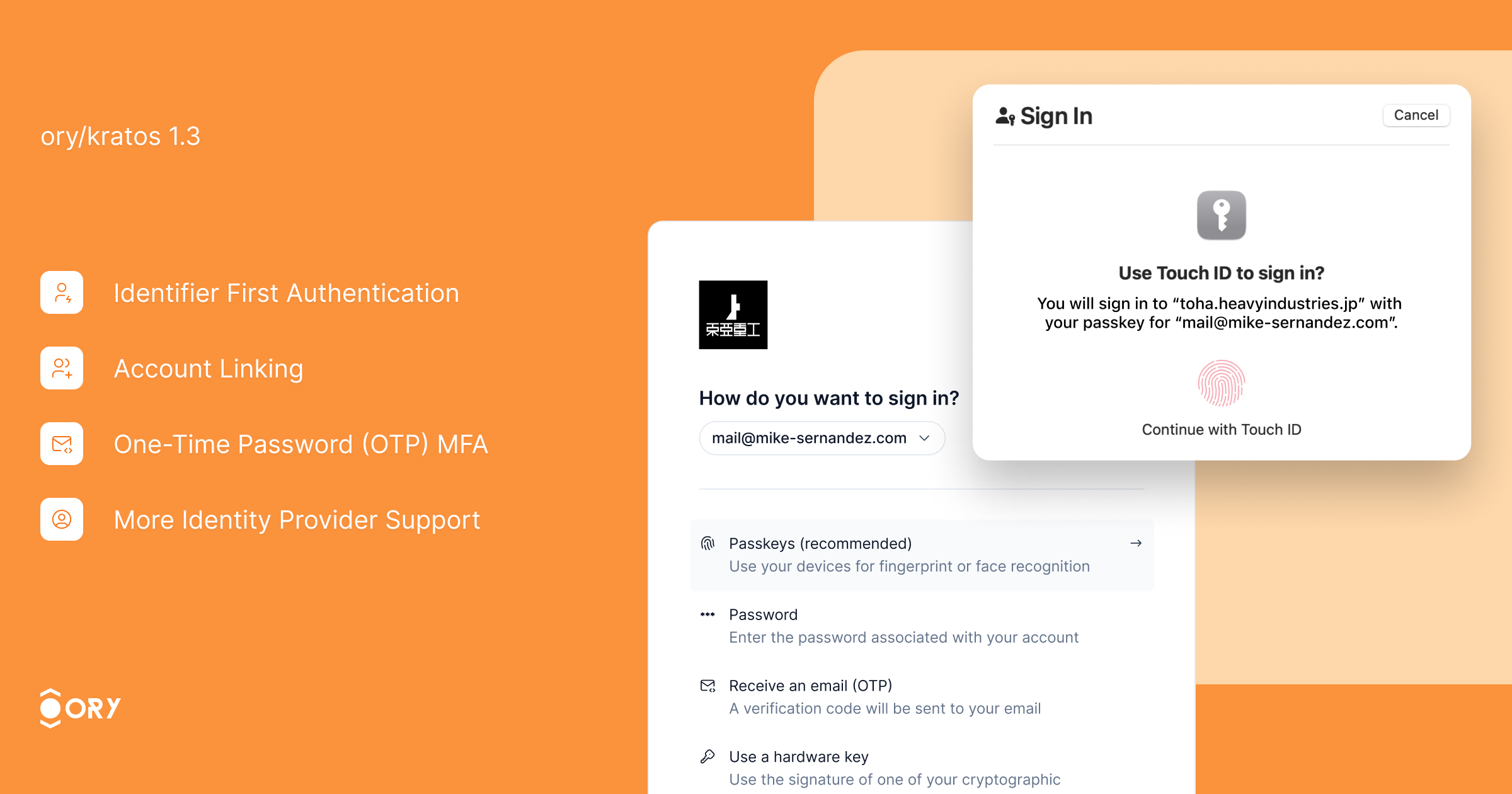 Enhance your sign-in experience with Identifier First Authentication. This feature allows users to first identify themselves (e.g., by providing their email or username) and then proceed with the chosen authentication method, whether it be OTP code, passkeys, passwords, or social login. By streamlining the sign-in process, users can select the authentication method that best suits their needs, reducing friction and enhancing security. Identifier First Authentication improves user flow and reduces the likelihood of errors, resulting in a more user-friendly and efficient login experience. 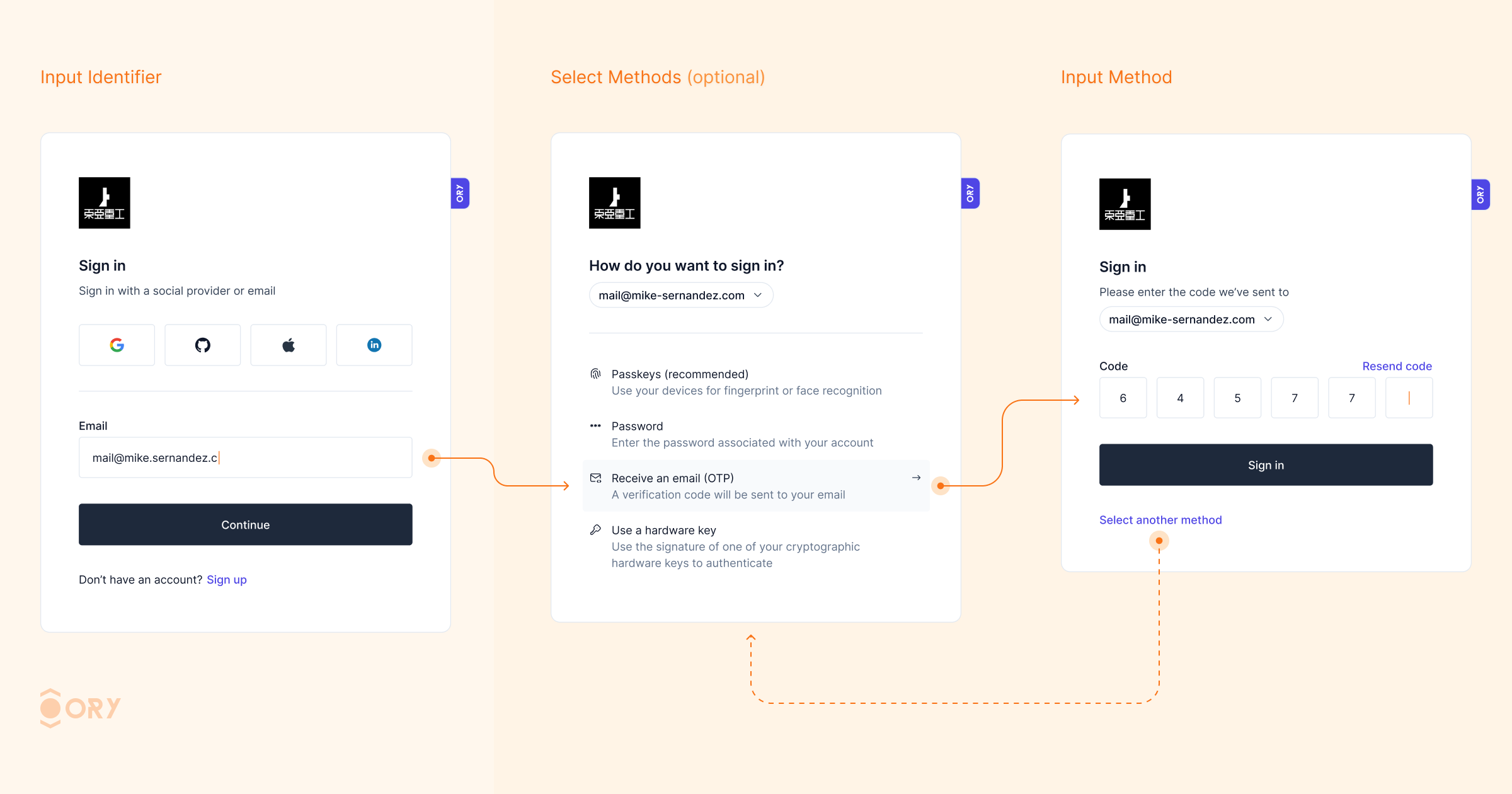 The UI for OpenID Connect (OIDC) account linking has been improved to provide better user guidance and error messages during the linking process. As a result, account linking error rates have dropped significantly, making it easier for users to link multiple identities (e.g., social login and email-based accounts) to the same profile. This improvement enhances user convenience, reduces support inquiries, and offers a seamless multi-account experience. You can now use Salesforce as an identity provider, expanding the range of supported identity providers. This integration allows organizations already using Salesforce for identity management to leverage their existing infrastructure, simplifying user management and enhancing the authentication experience. Social sign-in has been enhanced with better detection and handling of double-submit issues, especially for platforms like Facebook and Apple mobile login. These changes make the social login process more reliable, reducing errors and improving the user experience. Additionally, Ory Kratos now supports social providers in credential discovery, offering more flexibility during sign-up and sign-in flows. One-Time Password (OTP) MFA has been improved with more robust handling of code-based authentication. The enhancements ensure a smoother flow when using OTP for multi-factor authentication (MFA), providing clearer guidance to users and improving fallback mechanisms. These updates help to prevent users from being locked out due to misconfigurations or errors during the MFA process, increasing security without compromising user convenience. - **Deprecated `via` Parameter for SMS 2FA**: The `via` parameter is now deprecated when performing SMS 2FA. If not included, users will see all their phone/email addresses to perform the flow. This parameter will be removed in a future version. Ensure your identity schema has the appropriate code configuration for passwordless or 2FA login. - **Endpoint Change**: The `/admin/session/.../extend` endpoint will now return 204 No Content for new Ory Network projects. Returning 200 with the session body will be deprecated in future versions. - **SDK Enhancements**: Added new methods and support for additional actions in the SDK, improving integration capabilities. - **Password Migration Hook**: Added a password migration hook to facilitate migrating passwords where the hash is unavailable, easing the transition to Ory Kratos. - **Partially Failing Batch Inserts:** When batch-inserting multiple identities, conflicts or validation errors of a subset of identities in the batch still allow the rest of the identities to be inserted. The returned JSON contains the error details that led to the failure. - **Security Fixes**: Fixed a security vulnerability where the `code` method did not respect the `highest_available`setting. Refer to the [security advisory](https://github.com/ory/kratos/security/advisories/GHSA-wc43-73w7-x2f5) for more details. - **Session Extension Issues**: Fixed issues related to session extension to prevent long response times on `/session/whoami` when extending sessions simultaneously. - **OIDC and Social Sign-In**: Fixed UI and error handling for OpenID Connect and social sign-in flows, improving the overall experience. - **Credential Identifier Handling**: Corrected handling of code credential identifiers, ensuring proper detection of phone numbers and correct functioning of SMS/email MFA. - **Concurrent Updates for Webhooks**: Fixed concurrent map update issues for webhook headers, improving webhook reliability. - **Passwordless & 2FA Login**: Before upgrading, ensure your identity schema has the appropriate code configuration when using the code method for passwordless or 2FA login. - **Code Method for 2FA**: If you use the code method for 2FA or 1FA login but haven't configured the code identifier, set `selfservice.methods.code.config.missing_credential_fallback_enabled` to `true` to avoid user lockouts. We hope you enjoy the new features and improvements in Ory Kratos v1.3.0. Please remember to leave a [GitHub star](https://github.com/ory/kratos) and check out our other [open-source projects](https://github.com/ory). Your feedback is valuable to us, so join the [Ory community](https://slack.ory.sh/) and help us shape the future of identity management.