This project is mirrored from https://github.com/ory/kratos.git.
Pull mirroring updated .
-
-
v1.3.00a49fd05 · ·
We are thrilled to announce the release of [Ory Kratos v1.3.0](https://www.ory.sh/kratos)! This release includes significant updates, enhancements, and fixes to improve your experience with Ory Kratos. 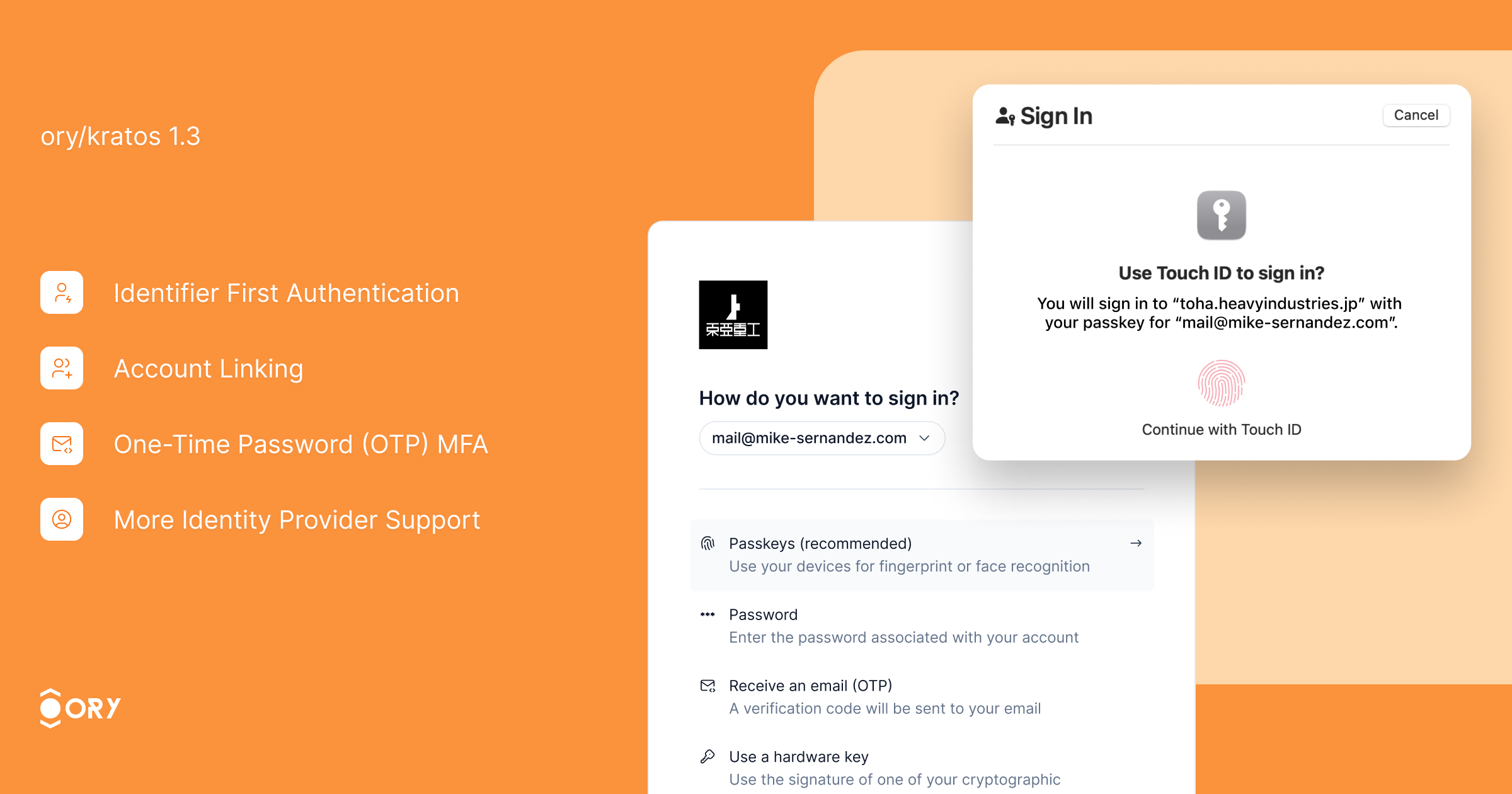 Enhance your sign-in experience with Identifier First Authentication. This feature allows users to first identify themselves (e.g., by providing their email or username) and then proceed with the chosen authentication method, whether it be OTP code, passkeys, passwords, or social login. By streamlining the sign-in process, users can select the authentication method that best suits their needs, reducing friction and enhancing security. Identifier First Authentication improves user flow and reduces the likelihood of errors, resulting in a more user-friendly and efficient login experience. 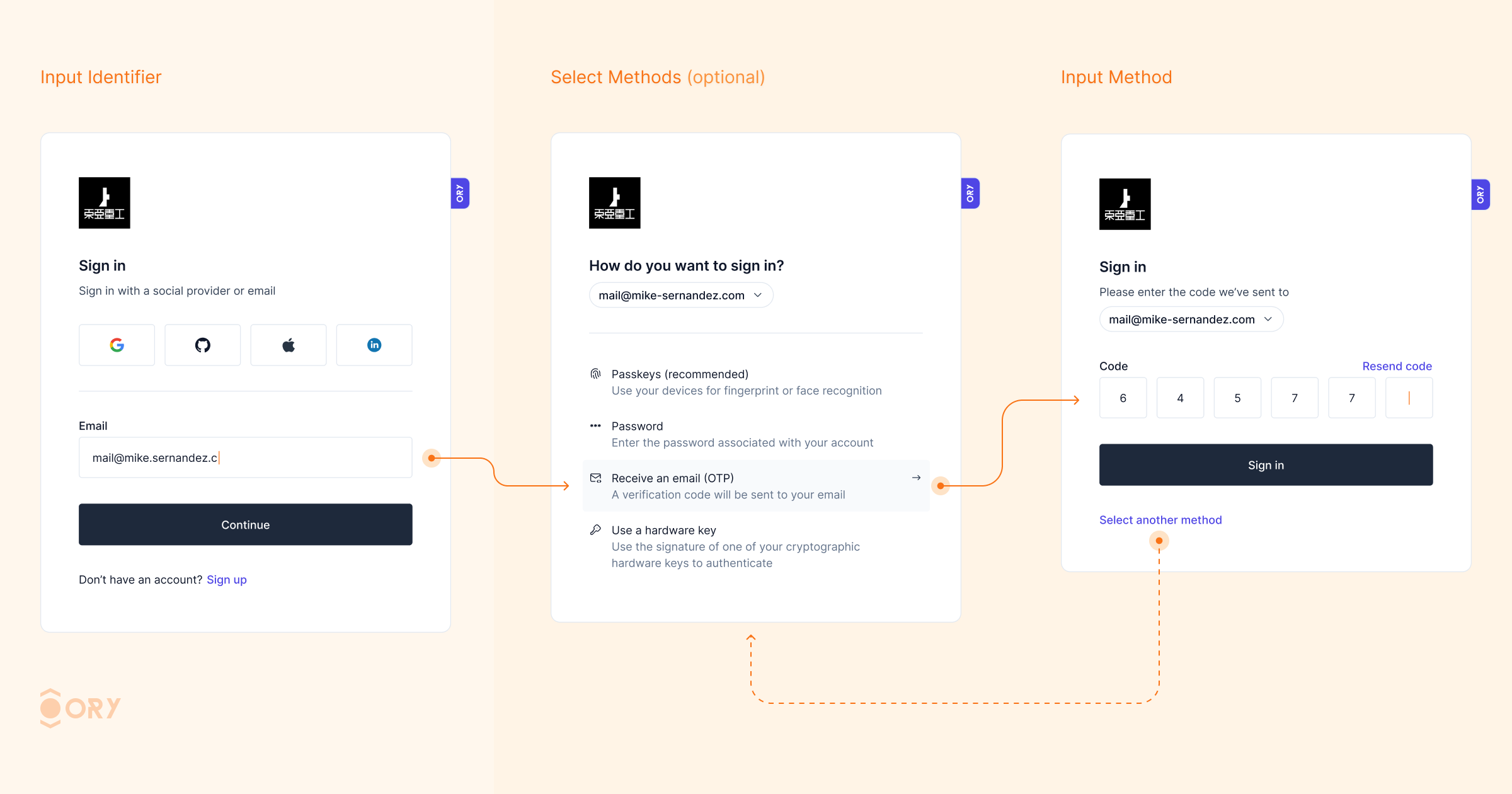 The UI for OpenID Connect (OIDC) account linking has been improved to provide better user guidance and error messages during the linking process. As a result, account linking error rates have dropped significantly, making it easier for users to link multiple identities (e.g., social login and email-based accounts) to the same profile. This improvement enhances user convenience, reduces support inquiries, and offers a seamless multi-account experience. You can now use Salesforce as an identity provider, expanding the range of supported identity providers. This integration allows organizations already using Salesforce for identity management to leverage their existing infrastructure, simplifying user management and enhancing the authentication experience. Social sign-in has been enhanced with better detection and handling of double-submit issues, especially for platforms like Facebook and Apple mobile login. These changes make the social login process more reliable, reducing errors and improving the user experience. Additionally, Ory Kratos now supports social providers in credential discovery, offering more flexibility during sign-up and sign-in flows. One-Time Password (OTP) MFA has been improved with more robust handling of code-based authentication. The enhancements ensure a smoother flow when using OTP for multi-factor authentication (MFA), providing clearer guidance to users and improving fallback mechanisms. These updates help to prevent users from being locked out due to misconfigurations or errors during the MFA process, increasing security without compromising user convenience. - **Deprecated `via` Parameter for SMS 2FA**: The `via` parameter is now deprecated when performing SMS 2FA. If not included, users will see all their phone/email addresses to perform the flow. This parameter will be removed in a future version. Ensure your identity schema has the appropriate code configuration for passwordless or 2FA login. - **Endpoint Change**: The `/admin/session/.../extend` endpoint will now return 204 No Content for new Ory Network projects. Returning 200 with the session body will be deprecated in future versions. - **SDK Enhancements**: Added new methods and support for additional actions in the SDK, improving integration capabilities. - **Password Migration Hook**: Added a password migration hook to facilitate migrating passwords where the hash is unavailable, easing the transition to Ory Kratos. - **Partially Failing Batch Inserts:** When batch-inserting multiple identities, conflicts or validation errors of a subset of identities in the batch still allow the rest of the identities to be inserted. The returned JSON contains the error details that led to the failure. - **Security Fixes**: Fixed a security vulnerability where the `code` method did not respect the `highest_available`setting. Refer to the [security advisory](https://github.com/ory/kratos/security/advisories/GHSA-wc43-73w7-x2f5) for more details. - **Session Extension Issues**: Fixed issues related to session extension to prevent long response times on `/session/whoami` when extending sessions simultaneously. - **OIDC and Social Sign-In**: Fixed UI and error handling for OpenID Connect and social sign-in flows, improving the overall experience. - **Credential Identifier Handling**: Corrected handling of code credential identifiers, ensuring proper detection of phone numbers and correct functioning of SMS/email MFA. - **Concurrent Updates for Webhooks**: Fixed concurrent map update issues for webhook headers, improving webhook reliability. - **Passwordless & 2FA Login**: Before upgrading, ensure your identity schema has the appropriate code configuration when using the code method for passwordless or 2FA login. - **Code Method for 2FA**: If you use the code method for 2FA or 1FA login but haven't configured the code identifier, set `selfservice.methods.code.config.missing_credential_fallback_enabled` to `true` to avoid user lockouts. We hope you enjoy the new features and improvements in Ory Kratos v1.3.0. Please remember to leave a [GitHub star](https://github.com/ory/kratos) and check out our other [open-source projects](https://github.com/ory). Your feedback is valuable to us, so join the [Ory community](https://slack.ory.sh/) and help us shape the future of identity management.
-
v1.3.0-pre.072aae5b6 · ·
-
v1.2.01a70648c · ·
Ory Kratos v1.2 is the most complete, scalable, and secure open-source identity server available. We are thrilled to announce its release! 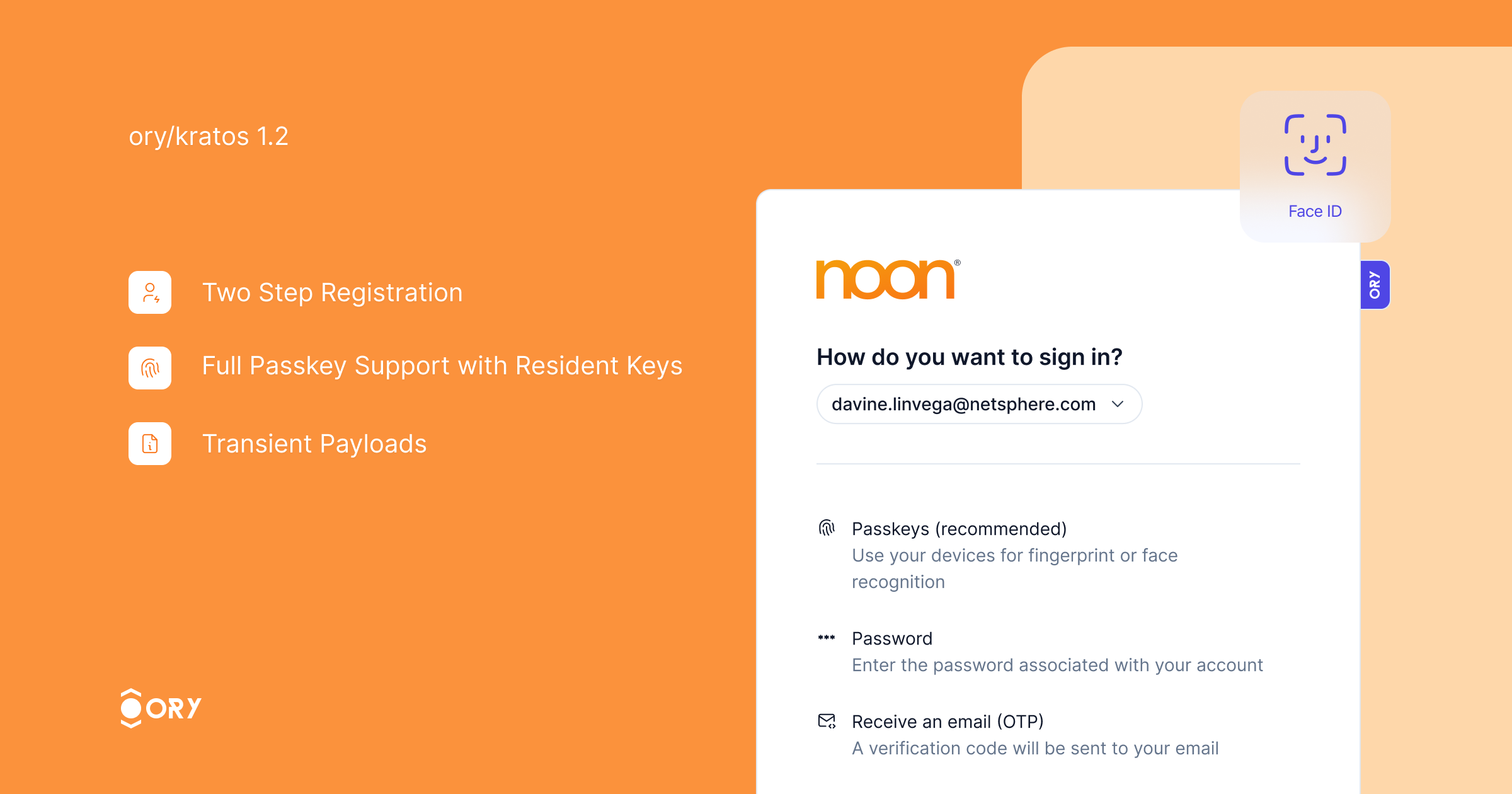 This release introduces two major features: two-step registration and full PassKey with resident key support. Passkeys provide a secure and convenient authentication method, eliminating the need for passwords while ensuring strong security. With this release, we have added support for resident keys, enabling offline authentication. Credential discovery allows users to link existing passkeys to their Ory account seamlessly. [Watch the PassKey demo video](https://github.com/aeneasr/web-next-deprecated/assets/3372410/e676c518-c82a-42a6-821e-28aecadb270c) Two-step registration improves the user experience by dividing the registration process into two steps. Users first enter their identity traits, and then choose a credential method for authentication, resulting in a streamlined process. This feature is especially useful when enabling multiple authentication strategies, as it eliminates the need to repeat identity traits for each strategy. 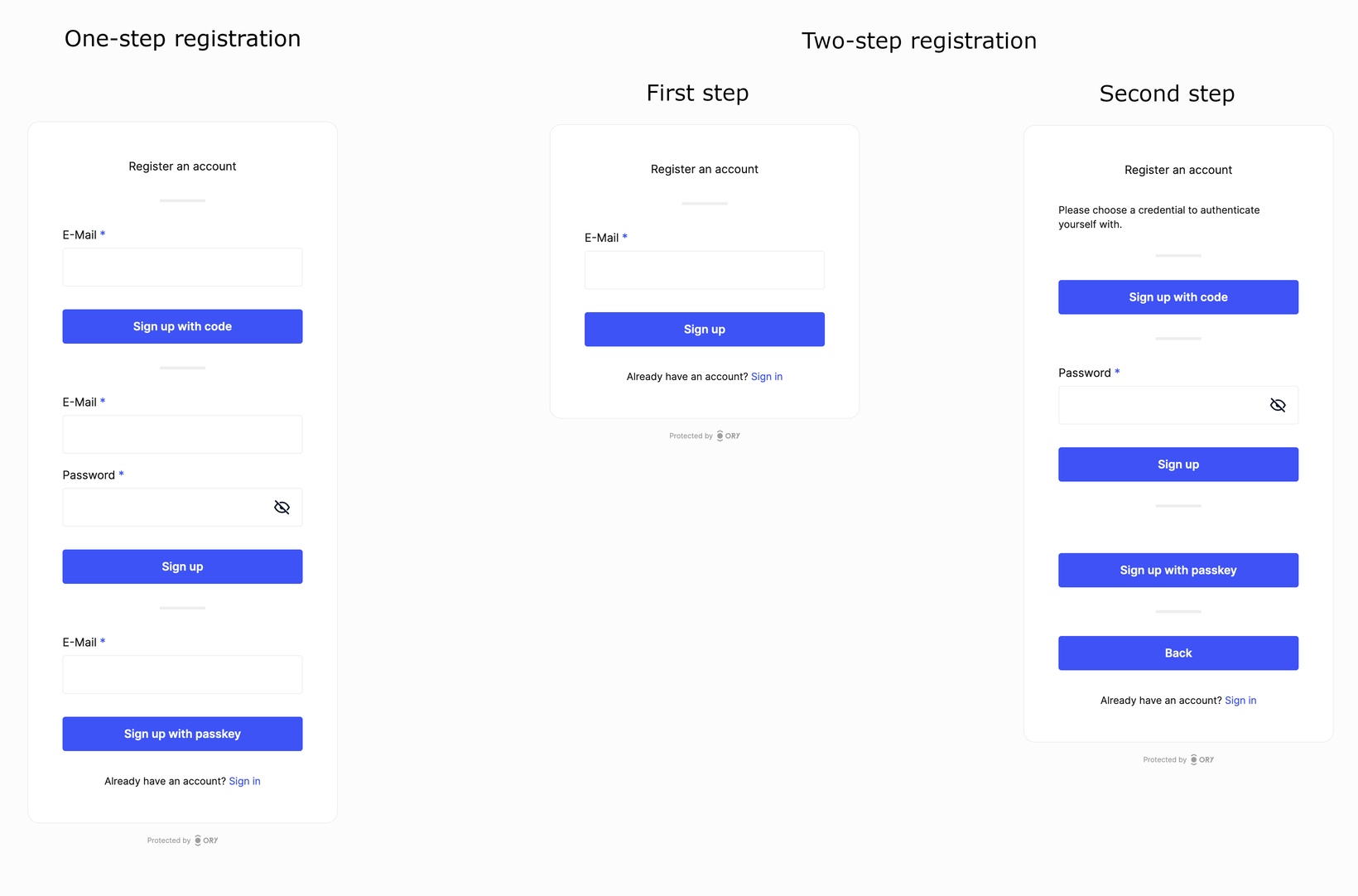 The 107 commits since v1.1 include several improvements: - **Webhooks** now carry session information if available. - **Transient Payloads** are now available across all self-service flows. - **Sign in with Twitter** is now available. - **Sign in with LinkedIn** now includes an additional v2 provider compatible with LinkedIn's new SSO API. - **Two-Step Registration**: An improved registration experience that separates entering profile information from choosing authentication methods. - **User Credentials Meta-Information** can now be included on the list endpoint. - **Social Sign-In** is now resilient to double-submit issues common with Facebook and Apple mobile login. **Two-Step Registration Enabled by Default**: This is now the default setting. To disable, set `selfservice.flows.registration.enable_legacy_flow` to `true`. - Improved account linking and credential discovery during sign-up. - The `return_to` parameter is now respected in OIDC API flows. - Adjustments to database indices. - Enhanced error messages for security violations. - Improved SDK types. - The `verification` and `verification_ui` hooks are now available in the login flow. - Webhooks now contain the correct identity state in the after-verification hook chain. We are doing this survey to find out how we can support self-hosted Ory users better. We strive to provide you with the best product and service possible and your feedback will help us understand what we're doing well and where we can improve to better meet your needs. We truly value your opinion and thank you in advance for taking the time to share your thoughts with us! Fill out the [survey now](https://share-eu1.hsforms.com/15DiCnJpcRuijnpAdnDhxxwextgn)!
-
v1.2.0-pre.02baecaee · ·
-
v1.1.0f47675b8 · ·
 Ory Kratos v1.1 is the most complete, most scalable, and most secure open-source identity server on the planet, and we are thrilled to announce its release! This release comes with over 270 commits and an incredible amount of new features and capabilities! - **Phone Verification & 2FA with SMS**: Enhance convenient security with phone verification and two-factor authentication (2FA) via SMS, integrating easily with SMS gateways like Twilio. This feature not only adds a convenient layer of security but also offers a straightforward method for user verification, increasing your trust in user accounts. - **Translations & Internationalization**: Ory Kratos now supports multiple languages, making it accessible to a global audience. This improvement enhances the user experience by providing a localized interface, ensuring users interact with the system in their preferred language. - **Native Support for Sign in with Google and Apple on Android/iOS**: Get more sign-ups with native support for "Sign in with Google" and "Sign in with Apple" on mobile platforms. Great user experience matters! - **Account Linking**: Simplify user management with new features that facilitate account linking. If a user registers with a password and later signs in with a social account sharing the same email, new screens make account linking straightforward, enhancing user convenience and reducing support inquiries. - **Passwordless "Magic Code"**: Introduce a passwordless login method with "Magic Code," which sends a one-time code to the user's email for sign-up and login. This method can also serve as a fallback when users forget their password or their social login is unavailable, streamlining the login process and improving user accessibility. - **Session to JWT Conversion**: Convert an Ory Session Cookie or Ory Session Token into a JSON Web Token (JWT), providing more flexibility in handling sessions and integrating with other systems. This feature allows for seamless authentication and authorization processes across different platforms and services. **Note:** To ensure a seamless upgrade experience with minimal impact, some of these features are gated behind the `feature_flags` config parameter, allowing controlled deployment and testing. The following features have been shipped exclusively to Ory Network for this version: - **[B2B SSO](https://www.ory.sh/docs/kratos/organizations)** allows your customers to connect their LDAP / Okta / AD / … to your login. Ory selects the correct login provider based on the user’s email domain. - [**Significantly better API performance](https://www.ory.sh/docs/api/eventual-consistency)** for expensive API operations by specifying the desired consistency (`strong`, `eventual`). - **Finding users effortlessly** with our new fuzzy search for credential identifiers available for the [Identity List API](https://www.ory.sh/docs/kratos/reference/api#tag/identity/operation/listIdentities). - Better reliability when sending out emails across different providers. - Streamlining the HTTP API and improving related SDK methods. - Better performance when calling the whoami API endpoint, updating identities, and listing identities. - The performance of listing identities has significantly improved with the introduction of keyset pagination. Page pagination is still available but will be fully deprecated soon. - Ability to list multiple identities in a batch call. - Passkeys and WebAuthn now support multiple origins, useful when working with subdomains. - The logout flow now redirects the user back to the `return_to` parameter set in the API call. - When updating their settings, the user was sometimes incorrectly asked to confirm the changes by providing their password. This issue has now been fixed. - When signing up with an account that already exists, the user will be shown a hint helping them sign in to their existing account. - CORS configuration can now be hot-reloaded. - The integration with Ory OAuth2 / Ory Hydra has improved for logout, login session management, verification, and recovery flows. - A new passwordless method has been added: "Magic code". It sends a one-time code to the user's email during sign-up and log-in. This method can additionally be used as a fallback login method when the user forgets their password. - Integration with social sign-in has improved, and it is now possible to use the email verified status from the social sign-in provider. - Ory Elements and the default Ory Account Experience are now internationalized with translations. - It is now possible to convert an Ory Session Cookie or Ory Session Token into a JSON Web Token. - Recovery on native apps has improved significantly and no longer requires the user to switch to a browser for the recovery step. - Administrators can now find users by their identifiers with fuzzy search - this feature is still in preview. - Importing HMAC-hashed passwords is now possible. - Webhooks can now update identity admin metadata. - New screens have been added to make account linking possible when a user has registered with a password and later tries signing in with a social account sharing the same email. - Ability to revoke all sessions of a user when they change their password. - Webhooks are now available for all login, registration, and login methods, including Passkeys, TOTP, and others. - The login screen now longer shows “ID” for the primary identifier, but instead extracts the correct label - for example, “Email” or “Username” from the Identity Schema. - Login hints help users with guidance when they are unable to sign in (wrong social sign-in provider) but have an active account. - Phone numbers can now be verified via an SMS gateway like Twilio. - SMS OTP is now a two-factor option. Ory Kratos 1.1 is a major release that marks a significant milestone in our journey. We sincerely hope that you find these new features and improvements in Ory Kratos 1.1 valuable for your projects. To experience the power of the latest release, we encourage you to get the latest version of Ory Kratos [here](https://github.com/ory/kratos) or leverage Ory Kratos in [Ory Network](https://www.ory.sh/network/) — the easiest, simplest, and most cost-effective way to run Ory. For organizations seeking to upgrade their self-hosted solution, **Ory offers enterprise support services to ensure a smooth transition**. Our team is ready to assist you throughout the migration process, ensuring uninterrupted access to the latest features and improvements. Additionally, we provide various [support plans](https://www.ory.sh/support/) specifically tailored for self-hosting organizations. These plans offer comprehensive assistance and guidance to optimize your Ory deployments and meet your unique requirements. We extend our heartfelt gratitude to the vibrant and supportive Ory Community. Without your constant support, feedback, and contributions, reaching this significant milestone would not have been possible. As we continue on this journey, your feedback and suggestions are invaluable to us. Together, we are shaping the future of identity management and authentication in the digital landscape. Contributors to this release in no particular order: [moose115](https://github.com/ory/kratos/commits?author=moose115), [K3das](https://github.com/ory/kratos/commits?author=K3das), [sidartha](https://github.com/ory/kratos/commits?author=sidartha), [efesler](https://github.com/ory/kratos/commits?author=efesler), [BrandonNoad](https://github.com/ory/kratos/commits?author=BrandonNoad) ,[Saancreed](https://github.com/ory/kratos/commits?author=Saancreed), [jpogorzelski](https://github.com/ory/kratos/commits?author=jpogorzelski), [dreksx](https://github.com/ory/kratos/commits?author=dreksx), [martinloesethjensen](https://github.com/ory/kratos/commits?author=martinloesethjensen), [cpoyatos1](https://github.com/ory/kratos/commits?author=cpoyatos1), [misamu](https://github.com/ory/kratos/commits?author=misamu), [tristankenney](https://github.com/ory/kratos/commits?author=tristankenney), [nxy7](https://github.com/ory/kratos/commits?author=nxy7), [anhnmt](https://github.com/ory/kratos/commits?author=anhnmt) Are you passionate about security and want to make a meaningful impact in one of the biggest open-source communities? Join the [Ory community](https://slack.ory.sh/) and become a part of the new ID stack. Together, we are building the next generation of IAM solutions that empower organizations and individuals to secure their identities effectively. Want to check out Ory Kratos yourself? Use these commands to get your Ory Kratos project running on the Ory Network: ``` brew install ory/tap/cli scoop bucket add ory <https://github.com/ory/scoop.git> scoop install ory bash <(curl <https://raw.githubusercontent.com/ory/meta/master/install.sh>) -b . ory sudo mv ./ory /usr/local/bin/ ory auth login ory create project --name "My first Kratos project" ory open account-experience registration ory patch identity-config \ --replace '/identity/default_schema_id="preset://username"' \ --replace '/identity/schemas=[{"id":"preset://username","url":"preset://username"}]' \ --format yaml ory open account-experience registration ``` -
v1.1.0-pre.01c3eeb71 · ·
-
v1.0.041b7c51c · ·
We are thrilled to announce Ory Kratos v1.0, the powerful Identity, User Management, and Authentication system! With this major update, Ory Kratos brings a host of enhancements and fixes that greatly improve the user experience and overall performance. Several compelling reasons led to label Ory Kratos as a major release, like successfully processing over 100 million API requests daily and having about 100 million Docker Pulls. We have maintained stability within the Ory Kratos APIs for nearly two years, demonstrating their robustness and reliability. No breaking changes mean that developers can trust the stability of Ory Kratos in production. Ory Kratos 1.0 introduces a variety of new features while focusing on stability, robustness, and improved performance. Major enhancements include support for social login and single-sign-on via OpenID connect in native apps, emails sent through HTTP rather than SMTP, and full compatibility with Ory Hydra v2.2.0. Users will also find multi-region support in the Ory Network for broader geographic reach, improved export functionality for all credential types, and enhanced session management with the introduction of the "provider ID" parameter. Other additions comprise distroless images for leaner resource utilization and faster deployment and support for the Lark OIDC provider. Significant improvements and fixes accompany these new features. Enhanced OIDC flows now include the ability to forward prompt upstream parameters, offering developers increased flexibility and customization options. The logout flow also supports the `return_to` parameter, facilitating more flexible redirection post-user logout. Performance has been a key focus, with Ory Kratos 1.0 now capable of handling hundreds of millions of active users monthly. Critical bug fixes have been applied to prevent users from being redirected to incorrect destinations, ensuring smoother authentication and authorization. Additionally, there's more support for legacy systems via implemented crypt(3) hashers and a fix for metadata patching has been deployed to ensure consistent user metadata management. For a detailed view of all changes, refer to the [changelog on GitHub]( https://github.com/ory/kratos/blob/master/CHANGELOG.md). Feedback and support are, as always, greatly appreciated. Ory Kratos 1.0 is a major release that marks a significant milestone in our journey. We sincerely hope that you find these new features and improvements in Ory Kratos 1.0 valuable for your projects. To experience the power of the latest release, we encourage you to get the latest version of Ory Kratos [here](https://github.com/ory/kratos) or leverage Kratos in [Ory Network](https://www.ory.sh/network/) — the easiest, simplest, and most cost-effective way to run Ory. For organizations seeking to upgrade their self-hosted solution, **Ory offers dedicated support services to ensure a smooth transition**. Our team is ready to assist you throughout the migration process, ensuring uninterrupted access to the latest features and improvements. Additionally, we provide various [support plans](https://www.ory.sh/support/) specifically tailored for self-hosting organizations. These plans offer comprehensive assistance and guidance to optimize your Ory deployments and meet your unique requirements. We extend our heartfelt gratitude to the vibrant and supportive Ory Community. Without your constant support, feedback, and contributions, reaching this significant milestone would not have been possible. As we continue on this journey, your feedback and suggestions are invaluable to us. Together, we are shaping the future of identity management and authentication in the digital landscape. Contributors to this release in alphabetical order: [borisroman](https://github.com/ory/kratos/commits?author=borisroman), [ci42](https://github.com/ory/kratos/commits?author=ci42), [CNLHC](https://github.com/ory/kratos/commits?author=CNLHC), [David-Wobrock](https://github.com/ory/kratos/commits?author=David-Wobrock), [giautm](https://github.com/ory/kratos/commits?author=giautm), [IchordeDionysos](https://github.com/ory/kratos/commits?author=IchordeDionysos), [indietyp](https://github.com/ory/kratos/commits?author=indietyp), [jossbnd](https://github.com/ory/kratos/commits?author=jossbnd), [kralicky](https://github.com/ory/kratos/commits?author=kralicky), [PhakornKiong](https://github.com/ory/kratos/commits?author=PhakornKiong), [sunakan](https://github.com/ory/kratos/commits?author=sunakan), [steverusso](https://github.com/ory/kratos/commits?author=steverusso) Are you passionate about security and want to make a meaningful impact in one of the biggest open-source communities? Join the [Ory community](https://slack.ory.sh) and become a part of the new ID stack. Together, we are building the next generation of IAM solutions that empower organizations and individuals to secure their identities effectively. Want to check out Ory Kratos yourself? Use these commands to get your Ory Kratos project running on the Ory Network: ```shell brew install ory/tap/cli scoop bucket add ory https://github.com/ory/scoop.git scoop install ory bash <(curl <https://raw.githubusercontent.com/ory/meta/master/install.sh>) -b . ory sudo mv ./ory /usr/local/bin/ ory auth ory create project --name "My first Kratos project" ory open account-experience registration ory patch identity-config \\ --replace '/identity/default_schema_id="preset://username"' \\ --replace '/identity/schemas=[{"id":"preset://username","url":"preset://username"}]' \\ --format yaml ory open account-experience registration ``` -
v1.0.0-pre.0ad271d24 · ·
-
-
v0.13.0349d0ee1 · ·
We’re excited to announce the release of Ory Kratos v0.13.0! This update brings many enhancements and fixes, improving the user experience and overall performance. Here are the highlights: - We’ve added new social sign-in options with Patreon OIDC and LinkedIn providers, making it even easier for your users to register and log in. Furthermore, we’ve introduced a new admin API that allows you to remove specific 2nd factor credentials, giving you more control over your user accounts. - Performance has been a key focus in this release. We’ve optimized the whoami calls, parallelized the getIdentity and getSession calls, and made asynchronous webhooks fully async. These improvements will result in faster response times and a smoother experience for your users. Additionally, we’ve implemented better tracing to help you diagnose and resolve issues more effectively. - We’ve also made several updates to the webhook system. A new response.parse configuration has been introduced, allowing you to update identity data during registration. This includes admin/public metadata, identity traits, enabling/disabling identity, and modifying verified/recovery addresses. Please note that can_interrupt is now deprecated in favor of response.parse. - Lastly, we’ve made several important fixes, such as resolving the wrong message ID on resend code buttons, implementing the offline scope as Google expects, and improving the OIDC flow on duplicate account registration. We’ve also added the ability to configure whether the system should notify unknown recipients when attempting to recover an account or verify an address, enhancing security with “anti-account-enumeration measures.” We hope you enjoy these new features and improvements in Ory Kratos v0.13.0! All features are already live on the Ory Network - the simplest, fastest and most scalable way to run Ory. Please note that the v0.12.0 release was skipped due to CI issues. Head over to the changelog at [https://github.com/ory/kratos/blob/master/CHANGELOG.md](https://github.com/ory/kratos/blob/master/CHANGELOG.md) to read all the details. As always, we appreciate your feedback and support!
-
v0.11.141595c52 · ·
* Fixed several bugs to improve overall stability. * Optimized performance for faster load times and smoother operation. * Improved tracing capabilities for better debugging and issue resolution. We are constantly working to improve Ory Kratos and this release is no exception. Thank you for using Ory and please let us know if you have any feedback or encounter any issues.
-
v0.11.059c30b68 · ·
The 2022 winter release of Ory Kratos is here, and we are extremely excited to share with you some of the highlights included: * Ory Kratos now supports verification and recovery codes, which replace are now the default strategy and should be used instead of magic links. * Import of MD5-hashed passwords is now supported. * Ory Kratos can now act as the login app for the Ory Hydra Consent & Login Flow using the `oauth2_provider.url` configuration value. * Ory Kratos' SDK is now released as version 1. Learn more in the [upgrade guide](https://www.ory.sh/docs/guides/upgrade/sdk-v1). * New APIs are available to manage Ory Sessions. * Ory Sessions now contain device information. * Added all claims to the Social Sign-In data mapper as well as the option to customize admin and public metadata. * Add webhooks that can block the request, useful to do some additional validation. * Add asynchronous webhooks which do not block the request. * A CLI helper to clean up stale data. Please read the changelog carefully to identify changes which might affect you. Always test upgrading with a copy of your production system before applying the upgrade in production.
-
-
-
-
-
v0.10.087e0de7a · ·
We achieved a major milestone - Ory Kratos is out of alpha! Ory Kratos had no major changes in the APIs for the last months and feel confident that no large breaking changes will need to be introduced in the near future. This release focuses on quality-of-live improvements, resolves several bugs, irons out developer experience issues, and introduces session renew capabilities!
-
-